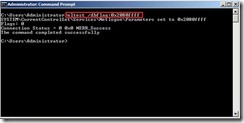
 Or add registry entity DBFlag on “HKLM\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters”
Or add registry entity DBFlag on “HKLM\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters” In the moment, I will use nlparse.exe this utility to analyze netlogon.log
In the moment, I will use nlparse.exe this utility to analyze netlogon.logOpen nlparse.exe by Run as administrator
 The error message will show up and tell us that component ‘comdlg32.ocx’ or one of its dependencies not correctly registered.
The error message will show up and tell us that component ‘comdlg32.ocx’ or one of its dependencies not correctly registered.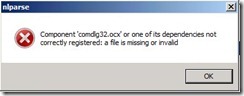 Search the related information about this error message by Google and find we can directly download VB6 Common Control comdlg32.ocx from this URL http://activex.microsoft.com/controls/vb6/comdlg32.CAB
Search the related information about this error message by Google and find we can directly download VB6 Common Control comdlg32.ocx from this URL http://activex.microsoft.com/controls/vb6/comdlg32.CABAfter download finish, double-click comdlg32.CAB this file next to copy comdlg32.ocx to C:\Windows\SysWOW64\
 Open command prompt by Run as Administrator, execute “regsvr32 c:\Windows\SysWOW64\comdlg32.ocx” to register cmdlg32.
Open command prompt by Run as Administrator, execute “regsvr32 c:\Windows\SysWOW64\comdlg32.ocx” to register cmdlg32.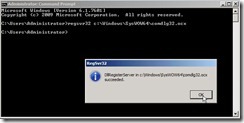 If it success, please run nlparse.exe again so that Netlogon-Parse GUI will show up normally now.
If it success, please run nlparse.exe again so that Netlogon-Parse GUI will show up normally now.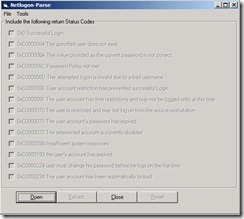 Click Open button
Click Open button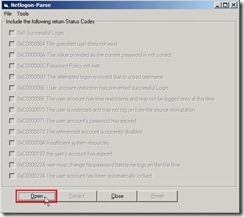 Expand C:\Windows\debug folder and select netlogon.log this file next to click Open button
Expand C:\Windows\debug folder and select netlogon.log this file next to click Open button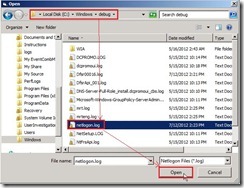 Enable 0xC000006A (no any record if authentication is Kerberos) and 0xC0000234 check box next to click Open button
Enable 0xC000006A (no any record if authentication is Kerberos) and 0xC0000234 check box next to click Open button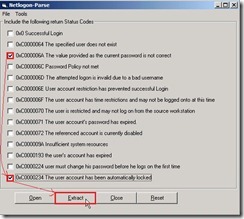 You will see the message as “C:\Windows\debug\netlogon.log Done!”
You will see the message as “C:\Windows\debug\netlogon.log Done!”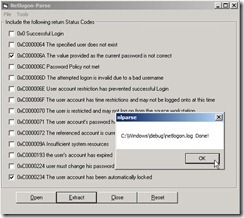 Under this folder C:\Windows\debug, there are generated two file with extension format as txt and csv.
Under this folder C:\Windows\debug, there are generated two file with extension format as txt and csv.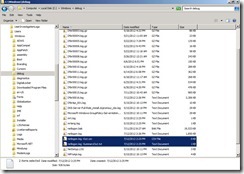 Now you can open these file to realize who is locked by which computer.
Now you can open these file to realize who is locked by which computer.Reference:
(1). Support Statement for Visual Basic 6.0 on Windows Vista, Windows Server 2008, Windows 7, and Windows 8
(2). If O.S. is 32bit, please copy comdlg32.ocx to C:\Windows\System32\(3). If the debug finish, please remember to disable NETLOGON record by command “nltest /dbflag:0x0” and restart netlogon service so that avoid the disk space overload.
<<< Account Lockout (part 3 of 4)
沒有留言:
張貼留言