For configuring Hyper-V replica, we have two authentication choice: Kerberos or Certificate. If use Kerberos authentication, the data transmitted from the primary to the replica server is not encrypted. For the date to be encrypted, we will use Certificate authentication and the certificate type has X.509v3 or self-signed. In this moment, we will introduce you how to deploy Hyper-V replica with self-signed certificate.
Due to Hyper-V Replica use machine level mutual authentication, we have to do the prerequisites of the certificate except for the steps about Kerberos authentication.
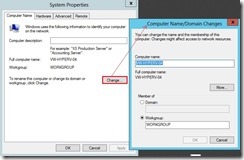
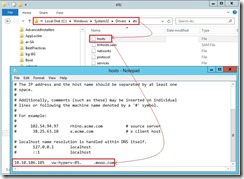
Add DNS suffix on Primary & Replica Node
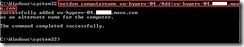
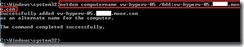
To use the command “NetDom computername” with parameter “/enumerate” (# 1) to realize what the computer name is.
 On Primary Node
On Primary Node
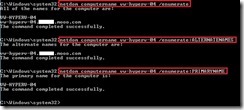
To add a new alternate by using the following command and the name must be a fully qualified DNS name (FQDN)
netdom computername vw-hyperv-04
/Add:vw-hyperv-04.xxx.mooo.com
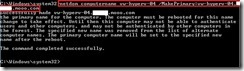
To make an existing alternate name into the primary name and the name must be a fully qualified DNS name (FQDN)
netdom computername vw-hyperv-04
/MakePrimary:vw-hyperv-04.xxx.mooo.com
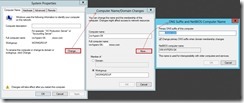
After reboot the system, the change will take effect and we can confirm by using the command “NetDom computername” with parameter "/enumerate” again.
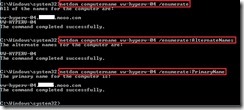
The “AS-IS” status of the DNS suffix
The “TO-BE” status of the DNS suffix
 On Replica Node
On Replica Node
To add a new alternate by using the following command and the name must be a fully qualified DNS name (FQDN)
netdom computername vw-hyperv-05
/Add:vw-hyperv-05.xxx.mooo.com
To make an existing alternate name into the primary name and the name must be a fully qualified DNS name (FQDN)
netdom computername vw-hyperv-05
/MakePrimary:vw-hyperv-05.xxx.mooo.com
 Open TCP 443 port on Primary & Replica NodesOn Primary Node
Open TCP 443 port on Primary & Replica NodesOn Primary Node
To enable HTTPS (port 443) replica traffic, we can run the following from an elevated command-prompt:
netsh advfirewall firewall set rule group="Hyper-V Replica HTTPS" new enable=yes
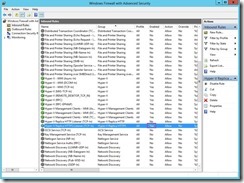
The “AS-IS” status of the firewall
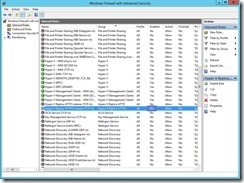
The “TO-BE” status of the firewall
 On Replica Node
On Replica Node
To enable HTTPS (port 443) replica traffic, we can run the following from an elevated command-prompt:
netsh advfirewall firewall set rule group="Hyper-V Replica HTTPS" new enable=yes Create self-signed certificate on Primary & Replica Nodes
On Primary Node
Create self-signed certificate on Primary & Replica Nodes
On Primary Node
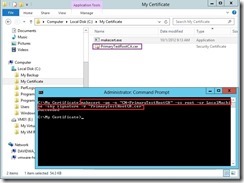
For creating a self-signed root authority certificate, we can run the following from an elevated command-prompt to install a Test certificate in the root store of the local machine and be saved as a file locally.
makecert -pe -n “CN=PrimaryTestRootCA
” -ss root -sr LocalMachine –sky signature -r “PrimaryTestRootCA.cer
”
For creating a new Test certificate, we can run the following elevated command to install a Client and Server certificate in the Personal store of the local machine and be saved as a file locally.
makecert -pe -n “CN=vw-hyperv-04.xxx.mooo.com
” -ss my –sr LocalMachine -sky exchange –eku 1.3.6.1.5.5.7.3.1,1.3.6.1.5.5.7.3.2 –in “PrimaryTestRootCA
” -is root -ir LocalMachine -sp “Microsoft RSA SChannel Cryptographic Provider” -sy 12 PrimaryTestCert.cer
 On Replica Node
On Replica Node
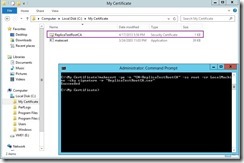
For creating a self-signed root authority certificate, we can run the following from an elevated command-prompt to install a Test certificate in the root store of the local machine and be saved as a file locally.
makecert -pe -n “CN=ReplicaTestRootCA
” -ss root -sr LocalMachine –sky signature -r “ReplicaTestRootCA.cer
”
The “AS-IS” status of the certificate
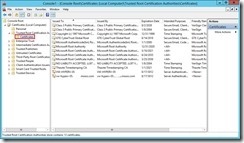
The “TO-BE” status of the certificate
For creating a new Test certificate, we can run the following elevated command to install a Client and Server certificate in the Personal store of the local machine and be saved as a file locally.
makecert -pe -n “CN=vw-hyperv-05.xxx.mooo.com
” -ss my –sr LocalMachine -sky exchange –eku 1.3.6.1.5.5.7.3.1,1.3.6.1.5.5.7.3.2 –in “ReplicaTestRootCA
” -is root -ir LocalMachine -sp “Microsoft RSA SChannel Cryptographic Provider” -sy 12 ReplicaTestCert.cer
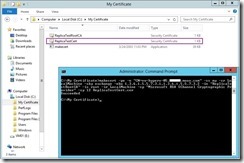
The “AS-IS” status of the certificate
The “TO-BE” status of the certificate
 Import a self-signed root CA into each node
On Primary Node
Import a self-signed root CA into each node
On Primary Node
Copy “ReplicaTestRootCA.cer” from the Replica server to the Primary server next to import self-signed Root CA by running the following command.
certutil -addstore -f Root “ReplicaTestRootCA.cer”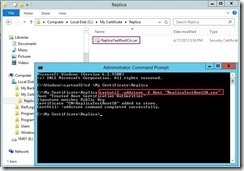
The “AS-IS” status of the root certificate
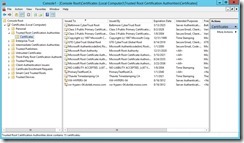
The “TO-BE” status of the root certificate
 On Replica Node
On Replica Node
Copy “PrimaryTestRootCA.cer” from the Primary server to the Replica server next to import self-signed Root CA by running the following command.
certutil -addstore -f Root “PrimaryTestRootCA.cer” Disable CRL check on each node
Disable CRL check on each node
Due to the self-signed certificate doesn’t support Revocation check, we have to modify the following registry key on each node for disabling the CRL check and reboot it.
reg add “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization\Replication” /v DisableCertRevocationCheck /d 1 /t REG_DWORD /f
The “AS-IS” status of the registry key
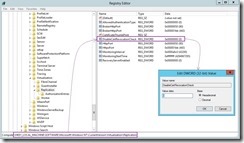
The “TO-BE” status of the registry key
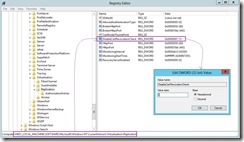 Validate certificate on each node
Validate certificate on each node
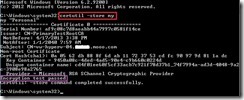
We can run the following command to realize whether this certificate validates on primary & replica server such as “Encryption test passed.
certutil –store my
Until now, we have already prepared the related prerequisite for certificate implement. In next article, we will begin to enable replication by using certificate based authentication.
Reference :
(# 1) The command “NetDom computername” is that manage the primary or alternate name for one Computer. A syntax is "
NetDom computername Computer
/enumerate[:{ALTERNATENAMES | PRIMARYNAME | ALLNAMES}]”
Parameters: /enumerate
ALTERNATENAMES Lists the alternate names only.
PRIMARYNAME Lists the primary name only.
ALLNAMES Lists the primary and any alternate names. This is the default.
(# 2) About where to get Makecert.exe, we can download/install
Windows SDK for Windows 7 on Windows 7 from Microsoft
and find it on Microsoft sdks directory “C:\Program Files (x86)\Microsoft SDKs\Windows\v7.xA\Bin\makecert.exe”
or directly download it from
http://www.inventec.ch/chdh/notes/makecert_5_131_3790_0.zip
When got this file, please Copy this File (makecert.exe) to C:\Windows\System32 or C:\Windows\sysWOW64 depending on the OS.
If want to realize this command in detail, please refer to
Makecert.exe (Certificate Creation Tool)
<<<
Hyper-V 3.0 --- Create VM that its virtual hard disk (VHDX) with parent-child relationship (part 8)
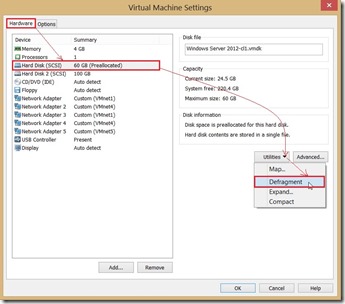 a warning message pop up and tell me that “Defragmentation failed: The specified virtual disk needs repair”.
a warning message pop up and tell me that “Defragmentation failed: The specified virtual disk needs repair”. Based on this warning sentence, I search the answer from the VMware KB and it is lucky for me to find out How to do it.
Based on this warning sentence, I search the answer from the VMware KB and it is lucky for me to find out How to do it. On the command prompt to run “vmware-vdiskmanager.exe -R “path of the vmdk file”
On the command prompt to run “vmware-vdiskmanager.exe -R “path of the vmdk file”
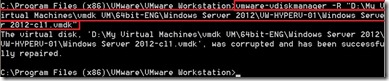 After redo the above operation for defragment, it will successfully complete now.
After redo the above operation for defragment, it will successfully complete now.


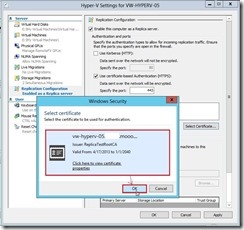
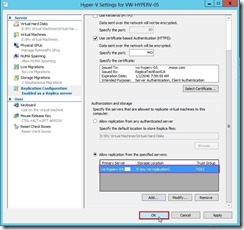
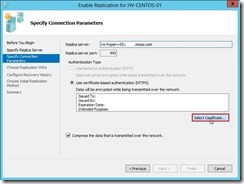
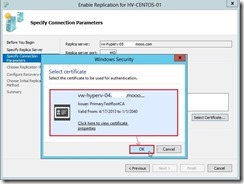
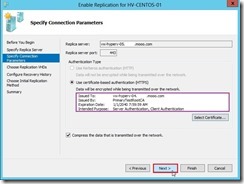
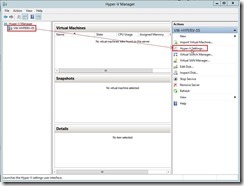 In Hyper-V Settings, select Replication Configuration Enabled as a Replica server and click Enable this computer as a Replica server check box. In Authentication and ports combo box, enable Use certificate-based Authentication (HTTPS) check box next to click Select Certificate… button
In Hyper-V Settings, select Replication Configuration Enabled as a Replica server and click Enable this computer as a Replica server check box. In Authentication and ports combo box, enable Use certificate-based Authentication (HTTPS) check box next to click Select Certificate… button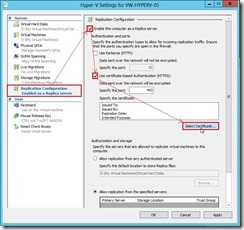
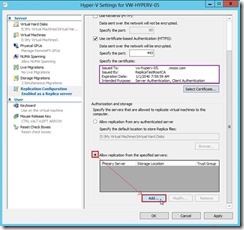
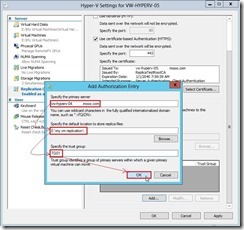

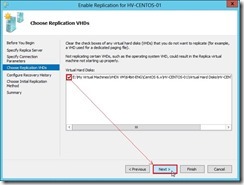
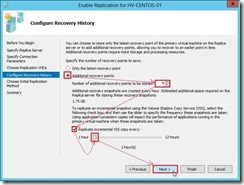
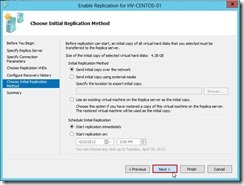
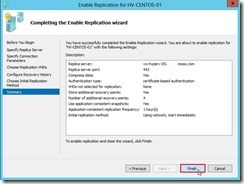
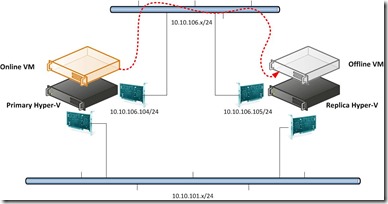
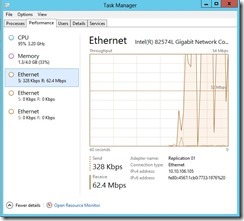
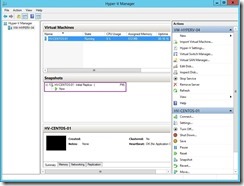 and the data delivery will go through the dedicated replication path until the replication finish.
and the data delivery will go through the dedicated replication path until the replication finish.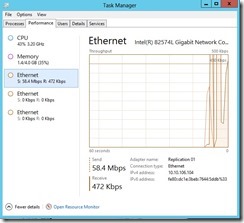
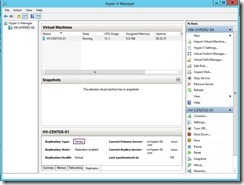

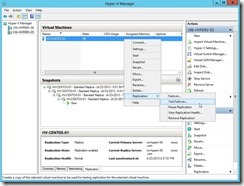
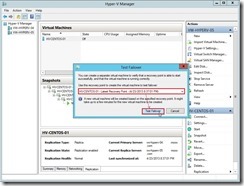
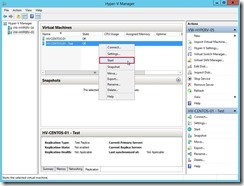 The temporary VM will be online and it doesn’t interrupt the ongoing replication & production VM on Primary node.
The temporary VM will be online and it doesn’t interrupt the ongoing replication & production VM on Primary node.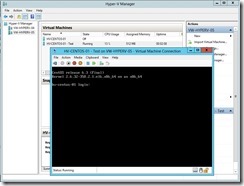



 After reboot the system, the change will take effect and we can confirm by using the command “NetDom computername” with parameter "/enumerate” again.
After reboot the system, the change will take effect and we can confirm by using the command “NetDom computername” with parameter "/enumerate” again.

























