月餅
一心一意念著您;
二話不說跑過去!
三言兩語說動您;
四頂花轎請回去!
五顏六色真美麗;
六神無主難決定!
七上八下終選定;
八成我倆有緣份!
九種口味別忘記;
十之八九真如意!
祝大家----中秋節快樂 ;-)
不必問我是誰,我就像您一樣:僅是位平凡人,但卻想在人生旅途上留下生活的足跡! 哪怕是過程跌跌撞撞、經歷風風雨雨,只要有您的關注,就是我最大的欣慰與成就!!! 感謝您的蒞臨:) 下一個職涯十年信念:不到最後關頭,決不輕言放棄!!!
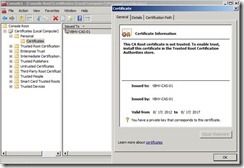 The Exchange self-signed certificate will have Subject Alternative Name (SANs) that correspond to the name of the Exchange server as the server name and the server’s fully qualified domain name.
The Exchange self-signed certificate will have Subject Alternative Name (SANs) that correspond to the name of the Exchange server as the server name and the server’s fully qualified domain name.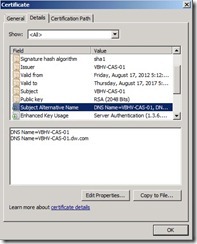 If we want to use the self-signed certificate, administrator need to do extra steps that let clients trust these certificate. In the moment, we will do a easy solution that get a certificate from an internal CA ---- Microsoft Activity Directory Certificate Services.
If we want to use the self-signed certificate, administrator need to do extra steps that let clients trust these certificate. In the moment, we will do a easy solution that get a certificate from an internal CA ---- Microsoft Activity Directory Certificate Services. On the Introduction page , provide a friendly name as “Adatum Exchange Server” for the certificate next to click Next > button
On the Introduction page , provide a friendly name as “Adatum Exchange Server” for the certificate next to click Next > button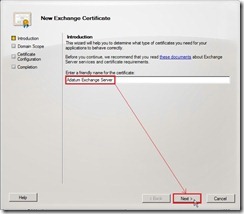 On the Domain Scope page, mark Enable wildcard certificate check box and then enter Root domain for wildcard as "*.adatum.com” or “adatum.com” due to we want to apply this certificate to all subdomains using wildcards. That is this option allows you to add subdomains without having to update an existing certificate in the future. (# 1)
On the Domain Scope page, mark Enable wildcard certificate check box and then enter Root domain for wildcard as "*.adatum.com” or “adatum.com” due to we want to apply this certificate to all subdomains using wildcards. That is this option allows you to add subdomains without having to update an existing certificate in the future. (# 1)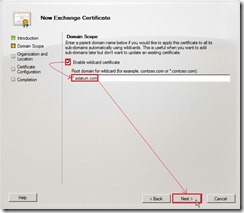 On the Organization and Location page, provide the related information next to click Browse… button for selecting Certificate Request File Path.
On the Organization and Location page, provide the related information next to click Browse… button for selecting Certificate Request File Path.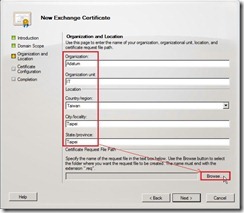 Select a path, provide file name with extension “.req” and then save it
Select a path, provide file name with extension “.req” and then save it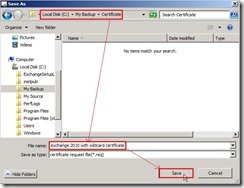 Click Next > button after the request file name is specifically created and selected.
Click Next > button after the request file name is specifically created and selected.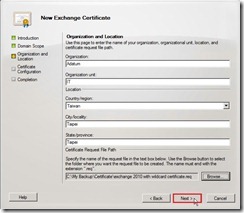 On the Certificate Configuration page, click New button to continue the process if Configuration Summary is true.
On the Certificate Configuration page, click New button to continue the process if Configuration Summary is true.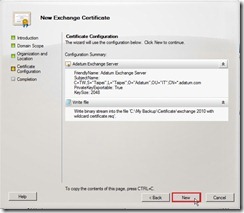 Click Finish button to close this wizard and continuously follow the step 1 to get the certificate issued from a CA.
Click Finish button to close this wizard and continuously follow the step 1 to get the certificate issued from a CA.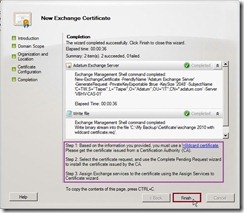 In the moment, a pending request certificate will be created. (# 2)
In the moment, a pending request certificate will be created. (# 2)
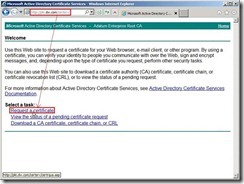 In the Request a Certificate page, click advanced certificate request
In the Request a Certificate page, click advanced certificate request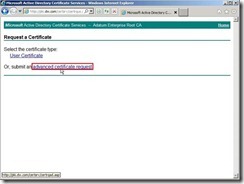 Click Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file because we have already generated the request on the Exchange Server 2010.
Click Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file because we have already generated the request on the Exchange Server 2010.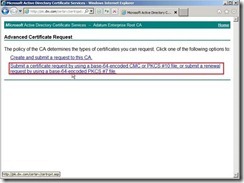 In the moment, please open the request file we generated earlier
In the moment, please open the request file we generated earlier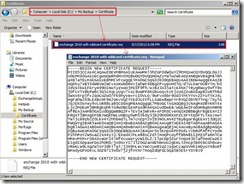 Select all content next to click Copy in menu
Select all content next to click Copy in menu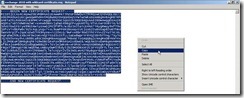 Paste it into the Base-64 encoded certificate request field
Paste it into the Base-64 encoded certificate request field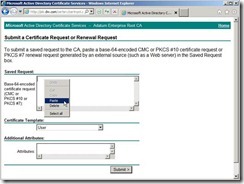 The result is as follows the diagram.
The result is as follows the diagram.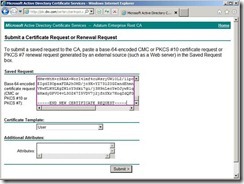 Set the certificate template to Web Server
Set the certificate template to Web Server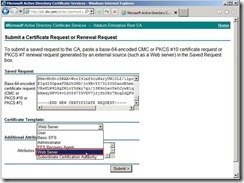 Click Submit > button to generate the request
Click Submit > button to generate the request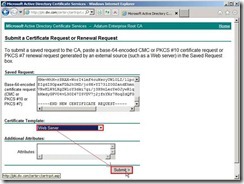 Select DER encoded next to click Download certificate to save this file to one path
Select DER encoded next to click Download certificate to save this file to one path
 Click Browse… button
Click Browse… button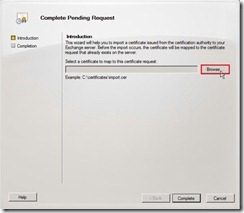 Select the certificate file that is downloaded earlier.
Select the certificate file that is downloaded earlier.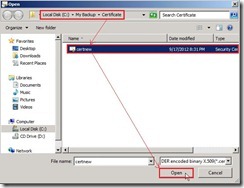 Click Complete button to import a certificate to the Exchange server
Click Complete button to import a certificate to the Exchange server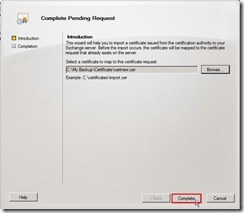 Click Finish button to close this wizard
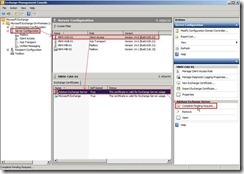
Click Finish button to close this wizard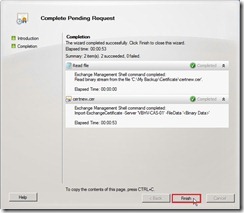 So does that will complete a pending certificate request (# 3) and is ready to be assigned to Exchange service.
So does that will complete a pending certificate request (# 3) and is ready to be assigned to Exchange service.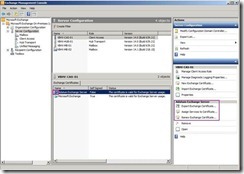
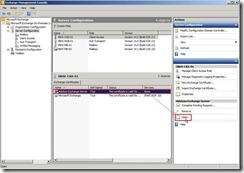 the certificate information tell us this CA Root certificate is not trusted and issued by point to itself.
the certificate information tell us this CA Root certificate is not trusted and issued by point to itself.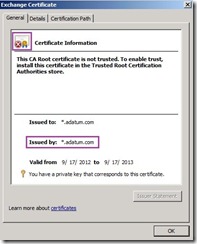 (# 3) When we select and open this request certificate again,
(# 3) When we select and open this request certificate again,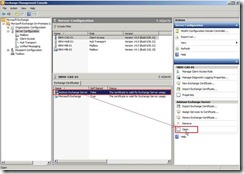 In General tab, the information issued by has already been changed to Root CA
In General tab, the information issued by has already been changed to Root CA 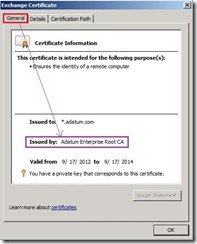 In Certification Path tab, its chain in top level also link to Root CA.
In Certification Path tab, its chain in top level also link to Root CA.
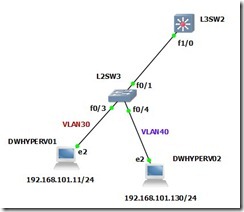
 In this network topology, when DW-HYPERV-01(192.168.101.11/24) ping DW-HYPERV-02(192.168.101.130/24) on command prompt, DW-HYPERV-02 can respond the message to DW-HYPERV-01, and vice verses.
In this network topology, when DW-HYPERV-01(192.168.101.11/24) ping DW-HYPERV-02(192.168.101.130/24) on command prompt, DW-HYPERV-02 can respond the message to DW-HYPERV-01, and vice verses.
 At first, we can realize what VLAN status is now by command line show vlan-switch
At first, we can realize what VLAN status is now by command line show vlan-switch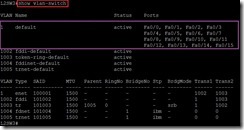 In the result, all Ethernet ports are active status and are assigned to VLAN 1. This is why PC can ping and the respond is normal each other.
In the result, all Ethernet ports are active status and are assigned to VLAN 1. This is why PC can ping and the respond is normal each other. So does that there is two new VLAN ID on Switch now.
So does that there is two new VLAN ID on Switch now. Finally, assign the Switch port number to the special VLAN ID
Finally, assign the Switch port number to the special VLAN ID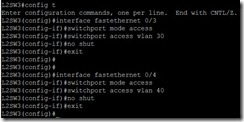 The port number will be mapped into VLAN ID one by one.
The port number will be mapped into VLAN ID one by one. In the moment, the message exchange fail between PCs each other.
In the moment, the message exchange fail between PCs each other.
