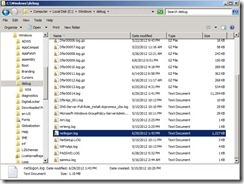
Configure DFSR
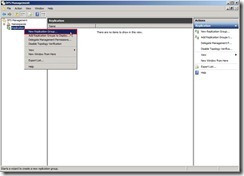
In DFS Management, right-click “Replication” and select “New Replication Group…” in menu to launch New Replication Group Wizard
 In New Replication Group Wizard, select the option of Replication Group Type as “Multipurpose replication group” next to click “Next >” button
In New Replication Group Wizard, select the option of Replication Group Type as “Multipurpose replication group” next to click “Next >” button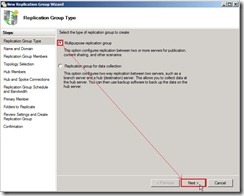 Write down the name of replication group as “One Way Replication with…” and Optional description of replication group as “Data replicate from DMZ to Internal”, select Domain as “dw.com” next to click “Next >” button
Write down the name of replication group as “One Way Replication with…” and Optional description of replication group as “Data replicate from DMZ to Internal”, select Domain as “dw.com” next to click “Next >” button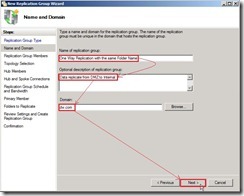 Click “Add…” button for selecting Replication Group Members
Click “Add…” button for selecting Replication Group Members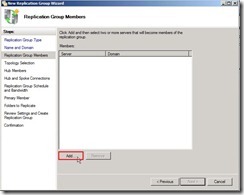 From this location “dw.com” to enter the object name as “VBHV-FS-01;VBHV-FS-11” next to click “Check Names” button
From this location “dw.com” to enter the object name as “VBHV-FS-01;VBHV-FS-11” next to click “Check Names” button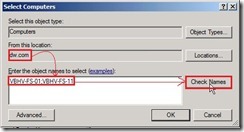 After the object names are resolved, please click “OK” button
After the object names are resolved, please click “OK” button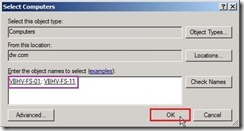 Check members progress now
Check members progress now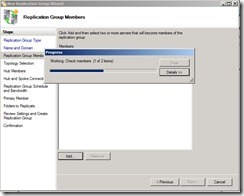 When the members have already added, click “Next >" button
When the members have already added, click “Next >" button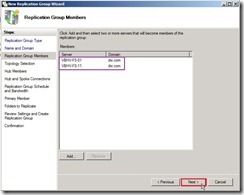 Due to I will create One-Way replication, select “No topology” option next to click “Next >” button
Due to I will create One-Way replication, select “No topology” option next to click “Next >” button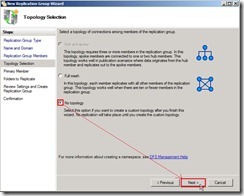 The warning message show up and tell us that the custom topology need to be created by ourselves after this wizard finishes.
The warning message show up and tell us that the custom topology need to be created by ourselves after this wizard finishes.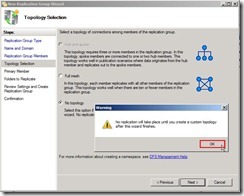 Select Primary member as “VBHV-FS-01” next to click “Next >” button
Select Primary member as “VBHV-FS-01” next to click “Next >” button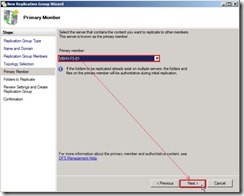 Click “Add…” button to select a folder on the primary member
Click “Add…” button to select a folder on the primary member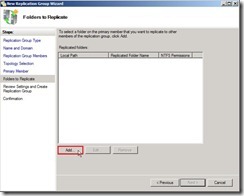 Click “Browse…” button for selecting local path of folder
Click “Browse…” button for selecting local path of folder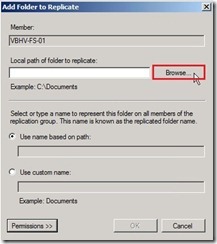 Select a folder as “DMZ to Internal” next to click “OK” button
Select a folder as “DMZ to Internal” next to click “OK” button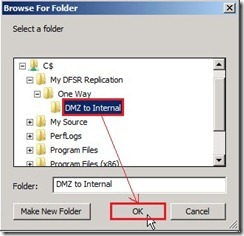 The Use name based on path option will be choose and name is “DMZ to Internal” as folder name. If doesn’t need to use custom name, please click “OK” button to go ahead.
The Use name based on path option will be choose and name is “DMZ to Internal” as folder name. If doesn’t need to use custom name, please click “OK” button to go ahead.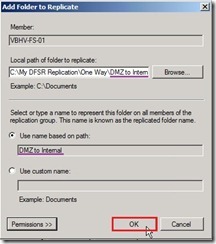 Click “Next >” button
Click “Next >” button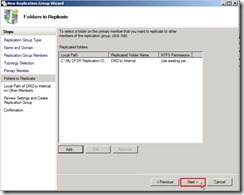 Click “Edit…” for selecting the local path of the replicated folder
Click “Edit…” for selecting the local path of the replicated folder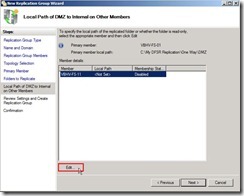 Select “Enabled” option next to click “Browse…” button
Select “Enabled” option next to click “Browse…” button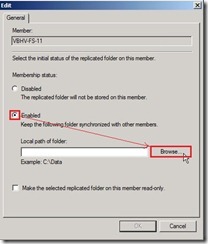 Select a folder as “DMZ to Internal” next to click “OK” button
Select a folder as “DMZ to Internal” next to click “OK” button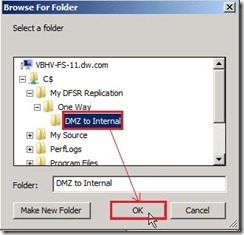 Click “OK” button
Click “OK” button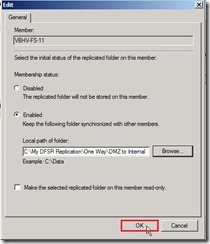 Click “Next >” button
Click “Next >” button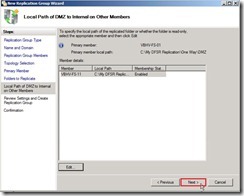 If the settings are correct, click “Create” button to begin to create the new replication group.
If the settings are correct, click “Create” button to begin to create the new replication group.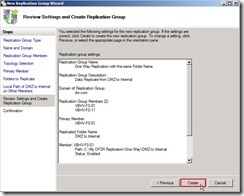 When the status show “Success” word, we have already completed the New Replication Group Wizard now.
When the status show “Success” word, we have already completed the New Replication Group Wizard now.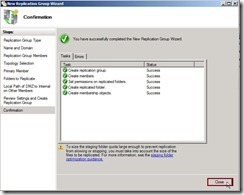 After click “Close” button, the warning message show up again and tell us that the replication never begin right now due to the configuration will depend on Active Directory Domain Services replication latency and polling interval.
After click “Close” button, the warning message show up again and tell us that the replication never begin right now due to the configuration will depend on Active Directory Domain Services replication latency and polling interval.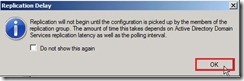 Now the DFS Management about Replication setting is as follows:
Now the DFS Management about Replication setting is as follows: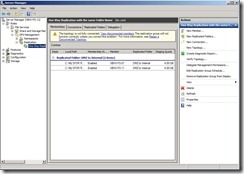 Due to only create one replication path from VBHV-FS-01 to VBHV-FS-11, the reverse path from VBHV-FS-11 to VBHV-FS-01 also need to be created so that the topology will be fully connected.
Due to only create one replication path from VBHV-FS-01 to VBHV-FS-11, the reverse path from VBHV-FS-11 to VBHV-FS-01 also need to be created so that the topology will be fully connected.Click “Connections” tab and “New Connection…” action
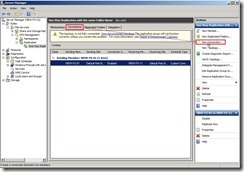 Change Sending member to “VBHV-FS-11” and Receiving member to “VBHV-FS-01”, disable “Create a second connection in the opposite direction” check box next to click “OK” button
Change Sending member to “VBHV-FS-11” and Receiving member to “VBHV-FS-01”, disable “Create a second connection in the opposite direction” check box next to click “OK” button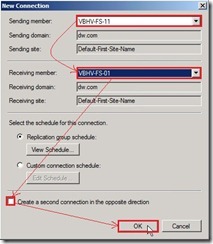 Now the reverse replication has already been created.
Now the reverse replication has already been created.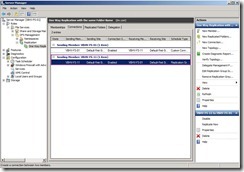 Click “Memberships” tab, right-click “VBHV-FS-11” next to select “Make read-only” in menu
Click “Memberships” tab, right-click “VBHV-FS-11” next to select “Make read-only” in menu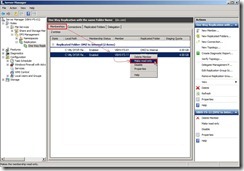 So do that will change Replicated Folder is read-only attribute.
So do that will change Replicated Folder is read-only attribute.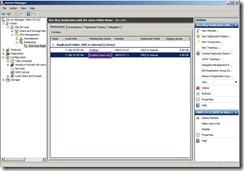 Until now, we have already completed the one-way DFSR configuration.
Until now, we have already completed the one-way DFSR configuration.In next article, I will confirm whether the replication function is normal.
<<< one-way DFSR on Windows Server 2008 R2 (part 1 of 3)
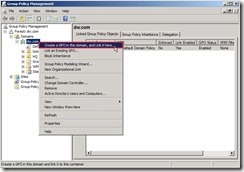
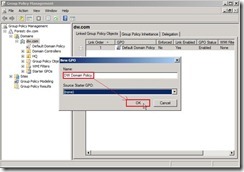
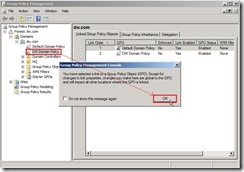
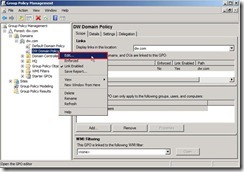
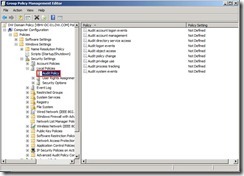
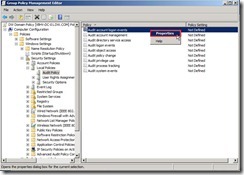

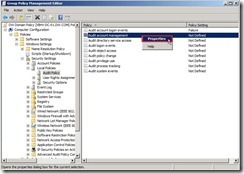
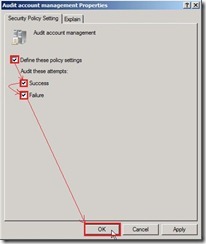
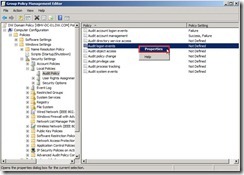

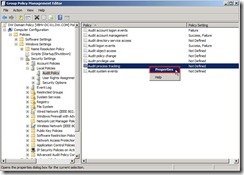
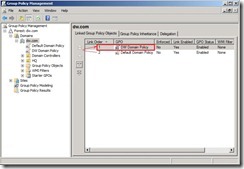
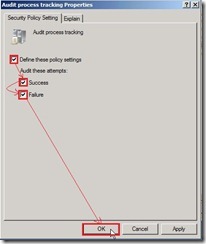 Finally, the audit policy setting is as follows:
Finally, the audit policy setting is as follows:
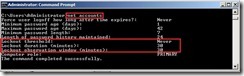
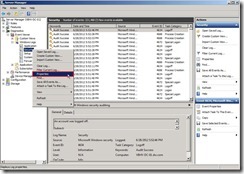
 Now the lockout policy will be changed by new GPO
Now the lockout policy will be changed by new GPO

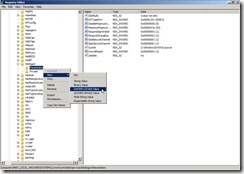 Double-click “DBFlag” to edit DWORD (32-bit) Value, that is to select “Hexadecimal” option, key in “2080FFFF” value data and click “OK” button
Double-click “DBFlag” to edit DWORD (32-bit) Value, that is to select “Hexadecimal” option, key in “2080FFFF” value data and click “OK” button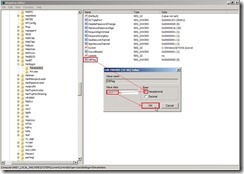

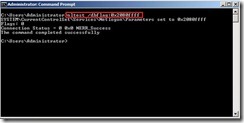 Note: After finish debugging, please run “nltest /dbflag:0x0” command to disable debug mode. Otherwise, maybe the netlogon.log file size will be over than the disk space in the future.
Note: After finish debugging, please run “nltest /dbflag:0x0” command to disable debug mode. Otherwise, maybe the netlogon.log file size will be over than the disk space in the future.