For clearly know the reason, I search the related information by Google and find out an old Tool from Microsoft --- Account Lockout and Management Tools. I decide to build a lab to realize whether it is helpful utility and what it help us.
In my lab environment, the DC is 64-bit Windows Server 2008 R2 and the client version is the same as DC.
In this article, I will introduce to prepare the prerequisite of system environment. The related procedure is as follows:
Audit Policy Setting in GPO
In any Domain Controller, click “Start” –> "Administrative Tools” –> “Group Policy Management” to open Group Policy Management
 Expand Forest/Domain tree and right-click the domain as “dw.com” to select “Create a GPO in this domain, and Link it here…” in menu
Expand Forest/Domain tree and right-click the domain as “dw.com” to select “Create a GPO in this domain, and Link it here…” in menu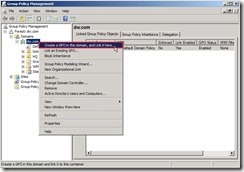 Key in new GPO name as “DW Domain Policy” next to click “OK” button
Key in new GPO name as “DW Domain Policy” next to click “OK” button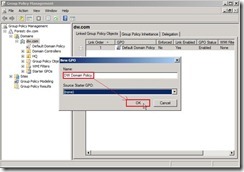 The new GPO as “DW Domain Policy” will be created now. When the mouse click it, the reminding message will show up. Please directly click “OK” button to ignore this message.
The new GPO as “DW Domain Policy” will be created now. When the mouse click it, the reminding message will show up. Please directly click “OK” button to ignore this message.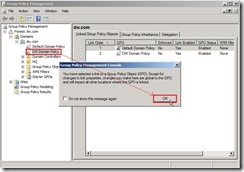 Right-click this new GPO and select “Edit…” in menu to open Group Policy Management Editor.
Right-click this new GPO and select “Edit…” in menu to open Group Policy Management Editor.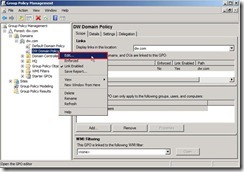 Expand “Computer Configuration” –> “Policies” –> “Windows Settings” –> "Security Settings” –> "Local Policies” and click “Audit Policy”, you will see all audit setting in the right panel.
Expand “Computer Configuration” –> “Policies” –> “Windows Settings” –> "Security Settings” –> "Local Policies” and click “Audit Policy”, you will see all audit setting in the right panel.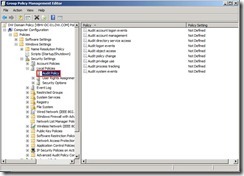 Right-click “Audit account logon events” and select “Properties” in menu
Right-click “Audit account logon events” and select “Properties” in menu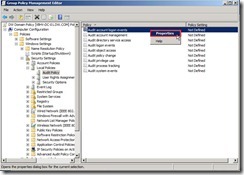 Enable “Define these policy settings / Failure” check box next to click “OK” button
Enable “Define these policy settings / Failure” check box next to click “OK” button Right-click “Audit account management” and select “Properties” in menu
Right-click “Audit account management” and select “Properties” in menu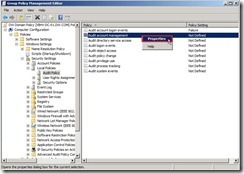 Enable “Define these policy settings / Success, Failure” check box next to click “OK” button
Enable “Define these policy settings / Success, Failure” check box next to click “OK” button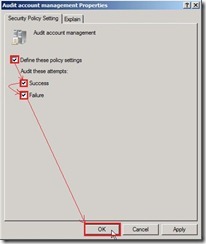 Right-click “Audit logon events” and select “Properties” in menu
Right-click “Audit logon events” and select “Properties” in menu Enable “Define these policy settings / Failure” check box next to click “OK” button
Enable “Define these policy settings / Failure” check box next to click “OK” button Right-click “Audit process tracking” and select “Properties” in menu
Right-click “Audit process tracking” and select “Properties” in menu Enable “Define these policy settings / Failure” check box next to click “OK” button
Enable “Define these policy settings / Failure” check box next to click “OK” button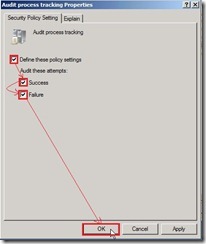 Finally, the audit policy setting is as follows:
Finally, the audit policy setting is as follows:
Change New GPO Priority
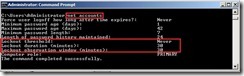
At a command prompt, type “net accounts” to realize lockout policy in the default GPO
 In Group Policy Management, change the order of new GPO as “DW Domain Policy” to the first order.
In Group Policy Management, change the order of new GPO as “DW Domain Policy” to the first order.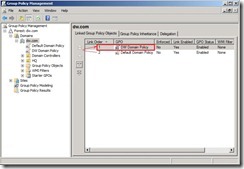 At a command prompt, type “gpupdate /force” to deploy policy right now
At a command prompt, type “gpupdate /force” to deploy policy right now Now the lockout policy will be changed by new GPO
Now the lockout policy will be changed by new GPO
Security Maximum log size setting in Event Viewer
In Event Viewer, right-click “Security” next to select “Properties” in menu.
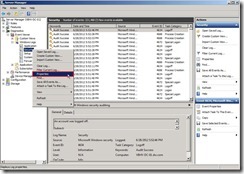 Change “Maximum log size” field to 200MB and select “Overwrite events as needed (oldest events first)” option next to click “OK” to correct this file size.
Change “Maximum log size” field to 200MB and select “Overwrite events as needed (oldest events first)” option next to click “OK” to correct this file size.
Enabling debug logging for the Net Logon serviceIn PDC Emulator of DC, there is two methods to enable it by KB 109626 --- Add Registry and Execute Command.
<Registry>
In “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters”, right-click “Parameters” and select “New” –> "DWORD (32-bit) Value” and key in “DBFlag” name
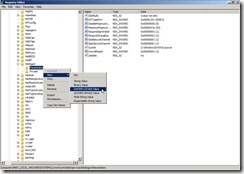 Double-click “DBFlag” to edit DWORD (32-bit) Value, that is to select “Hexadecimal” option, key in “2080FFFF” value data and click “OK” button
Double-click “DBFlag” to edit DWORD (32-bit) Value, that is to select “Hexadecimal” option, key in “2080FFFF” value data and click “OK” button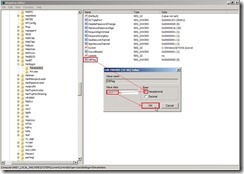 At a command prompt, type net stop netlogon, and then type net start netlogon. This enables debug logging.
At a command prompt, type net stop netlogon, and then type net start netlogon. This enables debug logging. <Command>
<Command>To do the command as “nltest /dbflag:0x2080ffff”
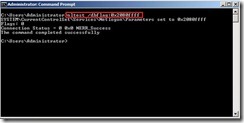 Note: After finish debugging, please run “nltest /dbflag:0x0” command to disable debug mode. Otherwise, maybe the netlogon.log file size will be over than the disk space in the future.
Note: After finish debugging, please run “nltest /dbflag:0x0” command to disable debug mode. Otherwise, maybe the netlogon.log file size will be over than the disk space in the future.
Until now, the system prerequisite is ready for me. In next article, I will make an scenario about account lockout next to use the utility to realize what can help us.
沒有留言:
張貼留言