This is why I want to rewrite this subject and push it on blogger!
Another reason, there is project in company also suffer this --- AD migrate from 2003 to 2008 R2.
After do it in the duration,we find out the Windows Platform cannot access Samba Share if the domain doesn't exist any windows 2003 AD. For realizing this status, I have to emulate the production environment in my Lab. That is why I need to know how to let Samba 3 join Windows 2008 R2 AD firstly.
After joining domain, I will test whether Windows can access Samba share and the AAA depend on AD next time. If it will success, I will post the procedure step by step on next blogger. I hope it will be true recently.
The following content record the process when I do it on my lab. Let it for your reference if you want to do the same thing in the future. Hope it can help you!!!
PS:
For simplify the Lab, I assume the firewall between Samba and AD doesn't be enabled. Of course,maybe it will confuse with practice environment for security concern. In the future, I will study how to do it next to correct this article.
[Lab Environment]
Windows Platform: (Forest function level and Domain function level = windows 2003)
First Domain Controller = Windows 2003 R2 Enterprise Server
Hostname = TEST-DC-00
IP Address = 10.10.102.11
Second Domain Controller = Windows 2008 R2 Enterprise Server
Hostname = TEST-DC-01
IP Address = 10.10.102.12
Linux Platform:
Samba Server = CentOS x86 6.0
Hostname = TESTSAMBA01
IP Address = 10.10.102.15
[Assumption]
[Assumption]
1. Disable firewall on Linux Platform
IPv4 iptables daemon disable
IPv6 iptables daemon disable
2. Disable firewall on Windows Platform
Windows 2003
Windows 2008 R2
[Prerequisite]
1. Confirm Samba Version
2. Install the necessary Samba package
[Comment]:
Samba version 3, version 3.4.3 or newer (Now Samba final version 3.5.8)
This is the latest stable release of Samba 3.4.3
Major enhancements in Samba 3.4.3 include:
o Fix trust relationships to windows 2008 (2008 r2) (bug #6711).
o Fix file corruption using smbclient with NT4 server (bug #6606).
o Fix Windows 7 share access (which defaults to NTLMv2) (bug #6680).
3. Install the necessary Kerberos libraries and tools
[Comment]:
MIT Kerberos 5, version 1.3.1 or newer
l Debian users need the krb5-user, krb5-config, krb5-doc, and
libkrb53 packages.
l Red Hat and Fedora users need the krb5 and krb5-client RPMs
4. Configure Kerberos
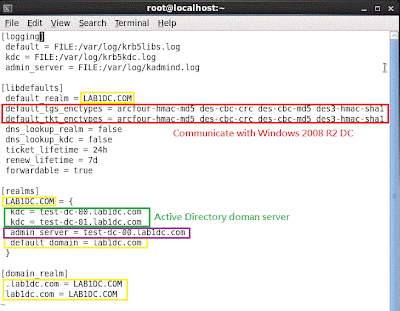
Please correct Kerberos configuration file, /etc/krb5.conf, as follows.
Try to connect for testing ticket
5. Change Linux hostname
Please correct network configuration file, /etc/sysconfig/network, as follows.
Please correct hosts configuration file, /etc/hosts, as follows.
Restart Network
6. Configure Samba
Please correct Samba configuration file, /etc/samba/smb.conf, as follows.
Check Smb.conf for syntax errors
7. Configure nsswitch.conf
Please correct Nsswitch configuration file, /etc/nsswitch.conf, as follows.
Verify whether the winbind is working
These commands pull lists of users and groups from AD
8. Configure PAM
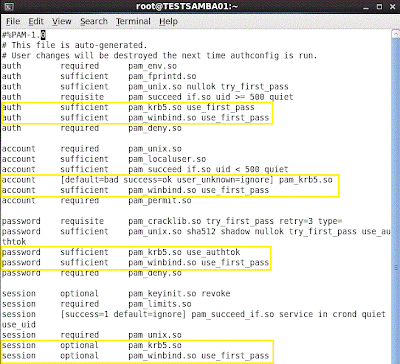
Please correct PAM configuration file, /etc/pam.d/system-auth-ac, as follows.
[Implement]
1. Join Samba to Active Directory
The Samba machine appear as a machine account under “Computers” in AD
2. Restart the smb and winbind services and set them to run at boot
3. Create keytab file for use with Kerberos
Restart SMB and WINBIND Daemon
1. Verify successfully to join the AD
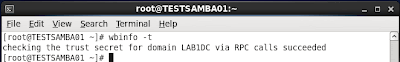
2. Check the secret between client and AD
3. Test the winbind authentication is working
4. Verify user account function